Forensic Accounting and Fraud Examination Terms:
- Accounting malpractice: Professional misconduct by an accountant or accounting firm.
- Audit: A systematic examination of financial records to ensure compliance with laws and regulations and the accuracy of financial statements.
- Consumer Fraud Schemes: Some of the more common types of fraud against consumers include:
-
- Advance fee fraud: This is when someone promises a large sum of money or a prize in exchange for an advance fee, such as a processing fee or taxes. The individual will never receive the promised money or prize and the fraudster will keep the advance fee.
- Health care fraud: This is when someone commits fraud related to health care services or products, such as billing for services that were never provided or providing unnecessary treatments.
- Identity theft: This occurs when someone uses another person’s personal information, such as their Social Security number or credit card information, to open bank accounts, credit cards, or loans in their name.
- Lottery and sweepstakes fraud: This is when scammers pose as legitimate lottery or sweepstakes organizations to trick individuals into paying money or providing personal information in order to claim a non-existent prize.
- Phishing scams: This is when someone poses as a legitimate organization, such as a bank or government agency, and attempts to trick individuals into giving them personal information or money.
- Ponzi scheme: A fraudulent investment scheme in which returns are paid to existing investors from funds contributed by new investors.
- Crime categories (general):
-
- Cybercrime: This includes crimes committed using the internet and technology, such as hacking and identity theft.
- Drug crime: This includes crimes such as possession, distribution, and trafficking of illegal drugs.
- Organized crime: This includes crimes committed by organized criminal groups, such as racketeering and extortion.
- Property crime: This includes crimes such as burglary, theft, and vandalism.
- Public order crime: This includes crimes that threaten public safety and order, such as disorderly conduct and loitering.
- Violent crime: This includes crimes such as murder, assault, and rape.
- White-collar crime: This includes crimes such as embezzlement, fraud, insider trading, and money laundering.

-
- Embezzlement: This includes crimes where someone misappropriates or misuses funds or property that have been entrusted to them, such as by a corporation, government agency or trust.
- Fraud: This includes any type of crime that involves deception, such as Ponzi schemes, credit card fraud, and insurance fraud.
- Insider trading: The illegal buying or selling of securities by individuals with access to non-public information.
- Money laundering: The process of disguising the proceeds of illegal activities as legitimate funds.
-
- Pre-fraud state of nature: This stage involves the perpetrator’s perception of their personal and professional situation, as well as their perception of the deterrence and detection fabric in place.
- Perceived opportunity: In this stage, the perpetrator identifies a perceived opportunity to commit fraud based on their pre-fraud state of nature.
- Rationalization: The perpetrator engages in rationalization, justifying the fraud to themselves and convincing themselves that it is acceptable or necessary.
- Action: The perpetrator takes action and carries out the fraud.
- Concealment: The perpetrator conceals the fraud, attempting to avoid detection or suspicion.
The Dorminey et al. meta-model emphasizes the importance of understanding the pre-fraud state of nature and the decision-making process of the perpetrator, in addition to the situational factors that create opportunities for fraud. By understanding the psychological and behavioral aspects of fraud, organizations can take a more proactive approach to fraud prevention and detection.

-
- Data analysis: Using data analysis tools, such as data mining and statistical analysis, to identify patterns of suspicious activity, such as unusual transactions or changes in spending patterns.
- Continuous monitoring: Implementing continuous monitoring systems that can identify and flag suspicious activity in real-time.
- Fraud detection software: Using specialized software that can detect patterns of fraudulent activity, such as abnormal behavior, anomalies and outliers in transaction data.
- Audit: Implementing regular internal and external audits of financial statements, financial transactions, and internal controls can help detect fraud early.
- Risk-based approach: Using a risk-based approach to fraud detection, which involves identifying and assessing potential fraud risks and focusing on areas of higher risk.
- Fraud investigation: Conducting internal investigations in response to suspected fraud, as well as working with external fraud investigators when necessary.
- Tip-offs: Encouraging employees, customers, and other stakeholders to report suspicious activity through a hotline or other reporting mechanism can help to identify potential fraud early on.
- Compliance: Ensuring compliance with laws and regulations related to fraud, such as the Foreign Corrupt Practices Act (FCPA) and the Sarbanes-Oxley Act (SOX), can help to reduce the risk of fraud and to minimize its impact if it occurs.
The Fraud Diamond consists of four components:
- Incentive/Pressure: The first component refers to the motivation or pressure that drives an individual to commit fraud. This can include financial pressures, such as debt or a desire for wealth, or non-financial pressures, such as a desire for power or prestige.
- Opportunity: The second component refers to the circumstances or conditions that create an opportunity for fraud to occur. This can include weaknesses in internal controls or financial systems, or a lack of oversight or monitoring.
- Rationalization/Attitude: The third component refers to the justifications or rationalizations that the fraudster makes to justify their behavior. This can include convincing themselves that their actions are justified, or that they will be able to repay the funds they have taken.
- Capability/Knowledge: The fourth component refers to the knowledge, skills, and abilities that the fraudster possesses to carry out the fraud. This can include technical knowledge of accounting or financial systems, as well as social skills such as the ability to manipulate others.
The Fraud Diamond model emphasizes the importance of understanding the complex interplay between these four components in the context of a specific fraud scheme. By identifying and addressing the incentives, opportunities, rationalizations, and capabilities that contribute to fraud, organizations can better prevent, detect, and respond to fraudulent activity.
-
- Corporate governance: Establishing strong corporate governance practices, such as having an independent board of directors and oversight committees, can help to ensure that the organization is managed in an ethical and transparent manner, and that there are checks and balances in place to prevent fraud.
- Hotline for reporting suspicious activity: Establishing a hotline or other mechanism for employees and other stakeholders to report suspicious activity can help to identify potential fraud early on and to take appropriate action.
- Inform employees about fraud and how to prevent it: Regularly training employees on how to recognize and prevent fraud can help to create a culture of integrity and to reduce the risk of fraud within the organization.
- Whistleblower policies: Having a whistleblower policy in place that protects employees who report suspected fraud can encourage employees to report suspicious activity and can help to create a culture of transparency and accountability.
- Auditing: implementing regular audits and reviews of financial statements, financial transactions, and internal controls can help detect fraud early and prevent it from happening.
- Risk management: Implementing a risk management program to identify and assess potential fraud risks, and to develop and implement preventive measures accordingly can help to protect the organization from fraud.
- Monitor and review: Regularly monitoring and reviewing the organization’s operations and financial records, can help detect early signs of fraud and prevent it from becoming a bigger problem.
- Compliance: Ensuring compliance with laws and regulations related to fraud, such as the Foreign Corrupt Practices Act (FCPA) and the Sarbanes-Oxley Act (SOX), can help to reduce the risk of fraud and to minimize its impact if it occurs.
- Employee training: Educating employees about the different types of fraud and how to recognize and prevent it can be an effective way to reduce the risk of fraud within an organization.
- Background checks: Conducting background checks on new employees, especially those who will handle sensitive information or financial transactions, can help to identify potential fraud risks.
- Internal controls: Implementing internal controls, such as segregation of duties and regular audits, can help to detect and prevent fraud.
- Fraud detection software: Using software that can detect patterns of fraudulent activity, such as unusual transactions or changes in spending patterns, can help to identify and prevent fraud.
- Two-factor authentication: This process of confirming the identity of a user by using a combination of two different forms of identification, such as a password and a fingerprint or a password and a code sent to a phone, can help to prevent unauthorized access to sensitive information.
- Data encryption: Encrypting sensitive data, such as credit card information, can help to protect it from being intercepted and used for fraud.
- Risk assessments: Regularly assessing and reassessing the risks of fraud and implementing preventive measures accordingly can help to identify and address potential vulnerabilities.
- Be vigilant: being aware of the common types of fraud, and being vigilant about checking financial statements, credit reports and other sensitive information can help prevent fraud from happening.

Fraud Tree (Government, Occupational, Corporate)
-
- Corruption:
- Conflicts of interest

- Purchasing schemes
- Sales Schemes
- Other
- Bribery: The offering, giving, receiving, or soliciting of something of value to influence the actions of an individual or organization.
- Invoice kickbacks: Illegal payments made to individuals or organizations in exchange for favorable treatment.
- Bid rigging
- Other
- Illegal gratuities:
- Economic extortion
- Conflicts of interest
- Asset Misappropriation:
- Cash

- Larcency A type of theft that involves taking possession of another person’s property with the intent to keep it permanently. This can include embezzlement, which is the unauthorized use of company funds or assets for personal gain.
- Of Cash on hand
- From the deposit
- Other
- Fraudulent disbursements Any unauthorized or illegal payments made by a company, typically involving the misuse of company funds. This can include check tampering, where an employee alters a check to change the payee or amount, or register disbursements, where an employee falsifies financial records to conceal the theft of company funds.
- Skimming: The theft of cash before it is recorded in financial records.
- Larcency A type of theft that involves taking possession of another person’s property with the intent to keep it permanently. This can include embezzlement, which is the unauthorized use of company funds or assets for personal gain.
- Inventory and Other Assets
- Misuse
- Larcency
- Asset requisitions and transfers
- False sales & shipping The submission of false or inflated invoices for goods or services that were not provided.
- Purchasing and receiving
- Unconcealed larceny
- Cash
- Financial statement fraud: The manipulation or falsification of financial statements to deceive investors or creditors.

- Financial
- Asset/revenue overstatements: Occur when a company falsely inflates the value of its assets or revenue in financial statements. This can be done to make the company appear more profitable than it actually is, or to deceive investors or creditors.
- Asset/revenue understatements: Asset and revenue understatements occur when a company falsely lowers the value of its assets or revenue in financial statements. This can be done to reduce the company’s tax liability, or to conceal financial losses.
- Non-Financial
- Employment credentials
- Internal documents
- External documents
- Financial
- Corruption:
-
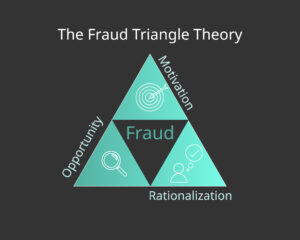
- Perceived Opportunity
- Perceived Pressure
- Rationalization
Ordinary people who commit these crimes are sometime referred to as accidental fraudsters
Researchers Wolfe and Hermanson (2004) argue the the Fraud Triangle should be expanded to include a fourth element, “capability,” which is described as an individual’s personal traits and abilities that play a major role in whether fraud may actually occur. The essential traits thought necessary for committing fraud, especially for large sums over long periods of time, include a combination of intelligence, position, ego, and the ability to deal well with stress. The person’s position or function within the organization may furnish the ability to create or exploit an opportunity for fraud.
People who steal not because they need money, because they think they can get away with it are not accidental fraudsters, they are predator fraudsters. Predators feel no pressure or a need to rationalize, they just look for opportunity. For this class of fraudster, researchers expanded the Fraud Triangle into a Fraud Diamond.

-
- Full name
- Social Security number
- Driver’s license number
- Passport number
- Address
- Phone number
- Email address
- Date of birth
- Financial account numbers
- Fingerprints or other biometric data
-
- Search engines: Search engines like Google, Bing, and Yahoo can be used to find information on individuals, companies, and organizations.
- Social media: Social media platforms like Facebook, LinkedIn, and Twitter can be used to gather information about individuals, such as their interests, connections, and activities.
- News and media: News websites and online media outlets can be used to gather information about current events and to track the activities of individuals and organizations.
- Government and regulatory websites: Websites such as the Securities and Exchange Commission (SEC) and the Financial Industry Regulatory Authority (FINRA) can be used to gather information about companies and individuals.
- Business and financial websites: Websites such as Bloomberg, Dun & Bradstreet, and Hoovers can be used to gather financial and business information about companies and individuals.
- Data and document repositories: Websites like LexisNexis and Westlaw can be used to access legal documents, such as court filings, and other types of public records.
- Darkweb: Websites like TOR can be used to access information that is not available through traditional search engines and web browsers.
- Intelligence software: Intelligence software can automate the collection of data from multiple sources, classify the data and present it in a way that is useful for the investigation.
The three elements of the Triangle of Fraud proposed by Albrecht are:
- Opportunity: The first element is opportunity, which refers to the circumstances that allow fraud to occur. This can include inadequate internal controls, lack of oversight, or other vulnerabilities that can be exploited by fraudsters.
- Rationalization/Conversion: The second element is rationalization or conversion, which refers to the mental processes that fraudsters use to justify their actions. This includes rationalizing the fraud as necessary or justified, and converting the fraud proceeds into a form that can be used or spent.
- The Act: The third element is the act itself, which refers to the actual commission of the fraud.
The Triangle of Fraud proposed by Albrecht emphasizes the importance of identifying opportunities for fraud and addressing them through stronger internal controls and oversight. Additionally, the concept of rationalization or conversion recognizes that fraudsters often justify their actions to themselves, and efforts must be made to address the underlying attitudes and behaviors that lead to fraud.

Links to other Glossaries
- Glossaries Home Page
- Data Analytics Terms
- Predictive Modeling Terms
- Mortgage and Mortgage-Backed Security Terms

